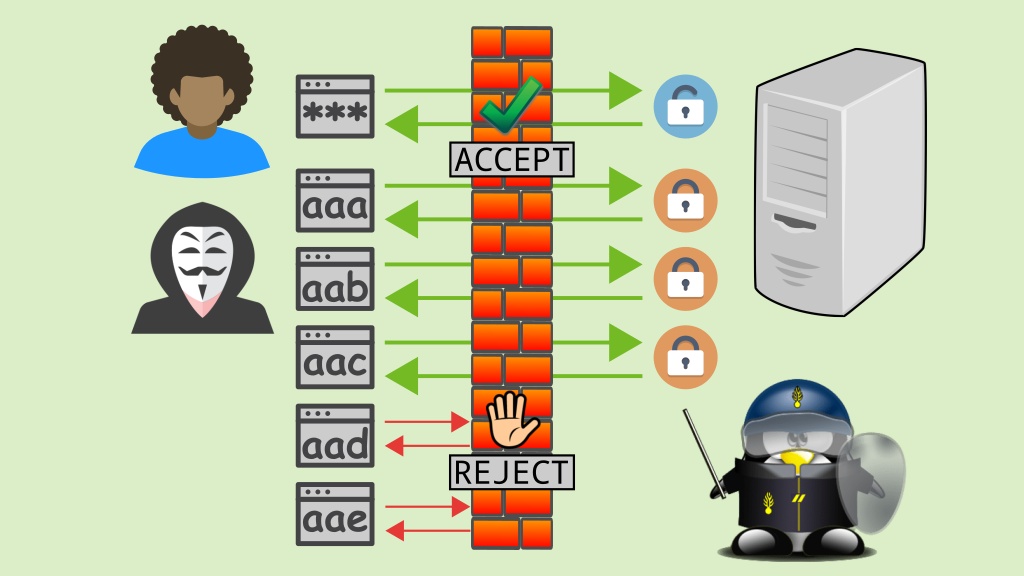
Commonly, restricted access systems authenticate their users by requesting a combination of username (a.k.a login) and password.A brute-force attack is a type of attack that consists in trying to guess a combination of username and password that grants access to a system. If an attacker knows at least an existing username, they are already halfway,...
Comments Read more ›