Digital certificates are used to identify and authenticate individuals, companies or computers on websites and systems. They ensure basic principles of information security, such as authenticity and non-repudiation, to data signed with them. Digitally signed documents are as legally valid as handwritten signed documents.
Digital certificates can be stored:
- as files in computers or mobile devices (common file extensions include
.crt,.cerand.pem); or - in cryptographic media, such as smart cards (which look like credit cards) or tokens (which look like USB sticks).
You need a smart card reader to use smart cards. USB tokens are standalone devices with a smart card chip inside (like a smart card reader with one non-removable smart card present).

A USB token looks like a USB stick, but it is a criptographic medium: it stores only digital certificates.
Many government and military websites require you to log in using a digital certificate.
US Department of Defense (DoD) limits access to many of its websites to be via a Common Access Card (CAC), a kind of smart card.
In Brazil, an example such a website is eCAC, a system of the Receita Federal (the Brazilian federal revenue service agency). Using that system, Brazilian citizens can consult information regarding their income tax declaration and refund, for instance.
There are also certificates that identify websites. When you visit a website that presents a valid digital certificate, your browser displays a green lock icon, indicating the page is authentic and secure. We have already talked about website certificates in another post.
In this post, you are going to see how to install support for smart cards and tokens on openSUSE Linux and how to log in to a government system using a digital certificate.
For future reference, here I use the openSUSE Leap 15.1 distribution.
I’m going to use the USB token presented on the image above, an eToken 5110, made by SafeNet (previously, Aladdin).
Smart cards and USB tokens are similar in functionality, installation and use, so through this post I refer to them interchangeably.
Installing the needed packages
On Linux, support for smart cards is provided mainly by the PC/SC and OpenSC softwares.
openSUSE users can install them running (as root):
1
# zypper in opensc pcsc-ccid pcsc-lite pcsc-tools
Start the PC/SC service, which makes smart cards available to applications:
1
# systemctl start pcscd
Also, enable the PC/SC service, so that it always gets started with the system:
1
# systemctl enable pcscd
You can verify the PC/SC service is running with:
1
2
3
4
5
6
7
8
9
10
11
# systemctl status pcscd
● pcscd.service - PC/SC Smart Card Daemon
Loaded: loaded (/usr/lib/systemd/system/pcscd.service; indirect; vendor preset: disabled)
Active: active (running) since Mon 2019-05-27 22:22:27 -03; 1h 23min ago
Docs: man:pcscd(8)
Main PID: 25347 (pcscd)
Tasks: 8 (limit: 4915)
CGroup: /system.slice/pcscd.service
└─25347 /usr/sbin/pcscd --foreground
May 27 22:22:27 viny-notebook systemd[1]: Started PC/SC Smart Card Daemon.
Plug in your token and make sure it is recognized as a USB device:
1
2
3
4
5
6
7
8
9
$ lsusb
Bus 003 Device 002: ID 8087:8001 Intel Corp.
Bus 003 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub
Bus 001 Device 007: ID 0bda:0129 Realtek Semiconductor Corp. RTS5129 Card Reader Controller
Bus 001 Device 006: ID 1bcf:2c81 Sunplus Innovation Technology Inc.
Bus 001 Device 005: ID 8087:0a2b Intel Corp.
Bus 001 Device 009: ID 0529:0620 Aladdin Knowledge Systems Token JC
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
My token appears in the penultimate line (0529:0620).
Verify that PC/SC recognizes your token with:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
$ pcsc_scan
Using reader plug'n play mechanism
Scanning present readers...
0: AKS ifdh [eToken 5110 SC] 00 00
Mon May 27 23:53:00 2019
Reader 0: AKS ifdh [eToken 5110 SC] 00 00
Event number: 0
Card state: Card inserted, Shared Mode,
ATR: 3B D5 18 00 81 31 FE 7D 80 73 C8 21 10 F4
ATR: 3B D5 18 00 81 31 FE 7D 80 73 C8 21 10 F4
+ TS = 3B --> Direct Convention
+ T0 = D5, Y(1): 1101, K: 5 (historical bytes)
TA(1) = 18 --> Fi=372, Di=12, 31 cycles/ETU
129032 bits/s at 4 MHz, fMax for Fi = 5 MHz => 161290 bits/s
TC(1) = 00 --> Extra guard time: 0
TD(1) = 81 --> Y(i+1) = 1000, Protocol T = 1
-----
TD(2) = 31 --> Y(i+1) = 0011, Protocol T = 1
-----
TA(3) = FE --> IFSC: 254
TB(3) = 7D --> Block Waiting Integer: 7 - Character Waiting Integer: 13
+ Historical bytes: 80 73 C8 21 10
Category indicator byte: 80 (compact TLV data object)
Tag: 7, len: 3 (card capabilities)
Selection methods: C8
- DF selection by full DF name
- DF selection by partial DF name
- Implicit DF selection
Data coding byte: 21
- Behaviour of write functions: proprietary
- Value 'FF' for the first byte of BER-TLV tag fields: invalid
- Data unit in quartets: 2
Command chaining, length fields and logical channels: 10
- Logical channel number assignment: by the card
- Maximum number of logical channels: 1
+ TCK = F4 (correct checksum)
Possibly identified card (using /usr/share/pcsc/smartcard_list.txt):
3B D5 18 00 81 31 FE 7D 80 73 C8 21 10 F4
Bank of Lithuania Identification card
Gemalto SafeNet eToken Java Based Cards
https://safenet.gemalto.com/multi-factor-authentication/authenticators/pki-usb-authentication/
That command does not stop, hit Ctrl + C to interrupt it.
Check if OpenSC finds your token:
1
2
3
4
$ opensc-tool -l
# Detected readers (pcsc)
Nr. Card Features Name
0 Yes AKS ifdh [eToken 5110 SC] 00 00
Specifics of Aladdin / SafeNet tokens
PC/SC and OpenSC are able to recognize SafeNet tokens, but not to manage them:
1
2
3
4
5
6
7
8
9
$ opensc-tool -n
Using reader with a card: AKS ifdh [eToken 5110 SC] 00 00
Unsupported card
$ opensc-tool -r 0 -f
SELECT FILE failed: Incorrect parameters in APDU
$ pkcs15-tool --reader 0 --list-pins
Failed to connect to card: Card is invalid or cannot be handled
Installing PC/SC and OpenSC, you should be ready to use most tokens, but to use SafeNet tokens you also need SafeNet Authentication Client (SAC), which is a proprietary software.
Ideally, you should get SAC from your token vendor, or from your certificate authority. In case they don’t provide you a Linux compatible version, you can google one.
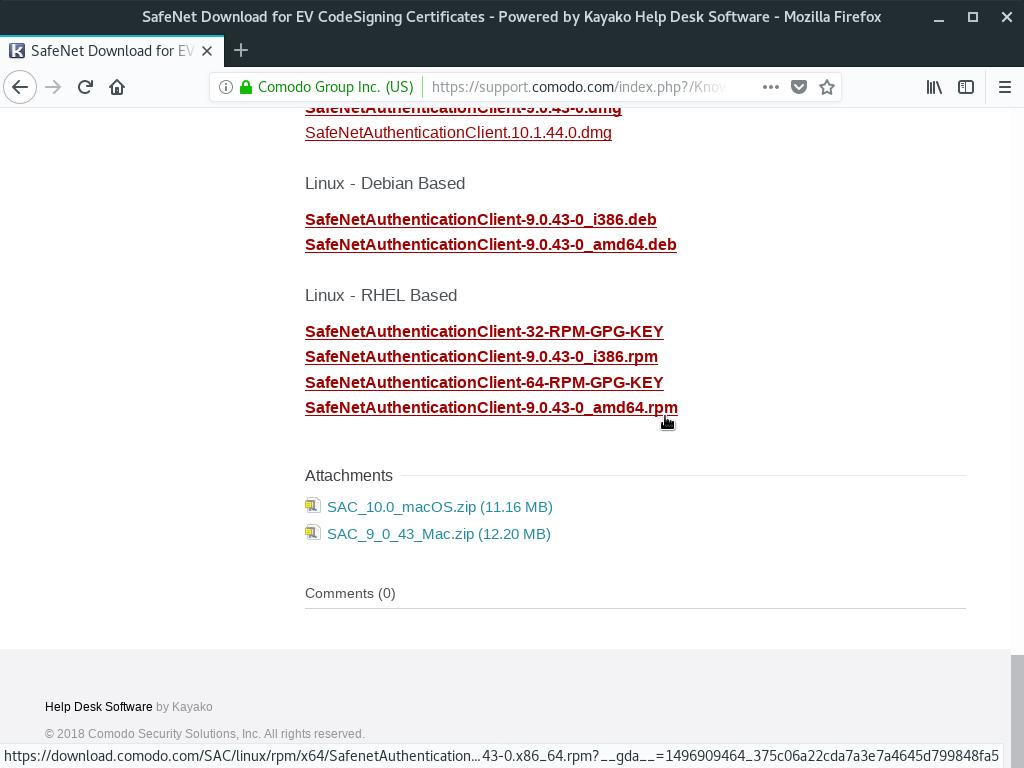
I found a RPM package on Comodo knowledgebase. Here, I’m going to use it.
Open this page and click on SafeNetAuthenticationClient-9.0.43-0_amd64.rpm, by the end:
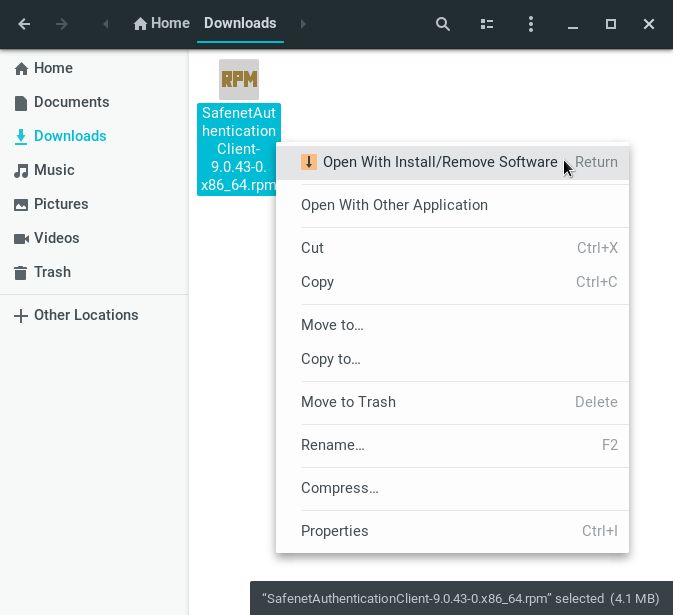
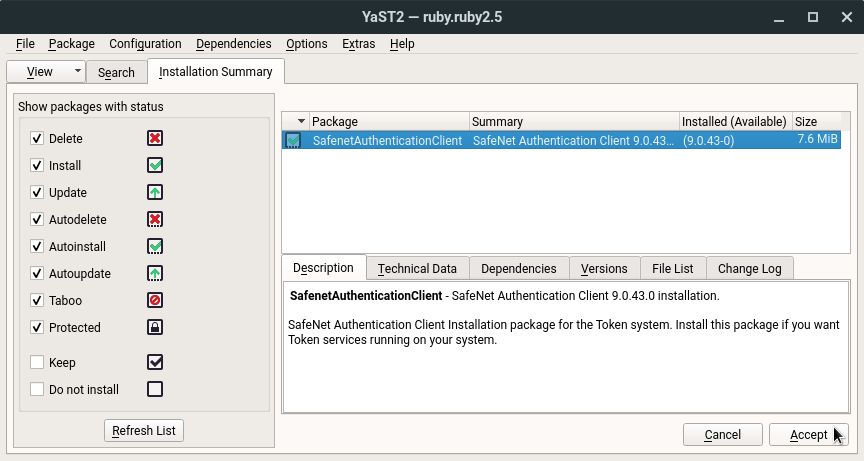
Install the downloaded RPM package using YaST’s Install/Remove Software:
I don’t know why that RPM package does not declare some libraries it requires. You need to install them manually:
1
2
# zypper in libcrypto43 openssl
# ln -s /usr/lib64/libcrypto.so.1.1 /usr/lib64/libcrypto.so.6
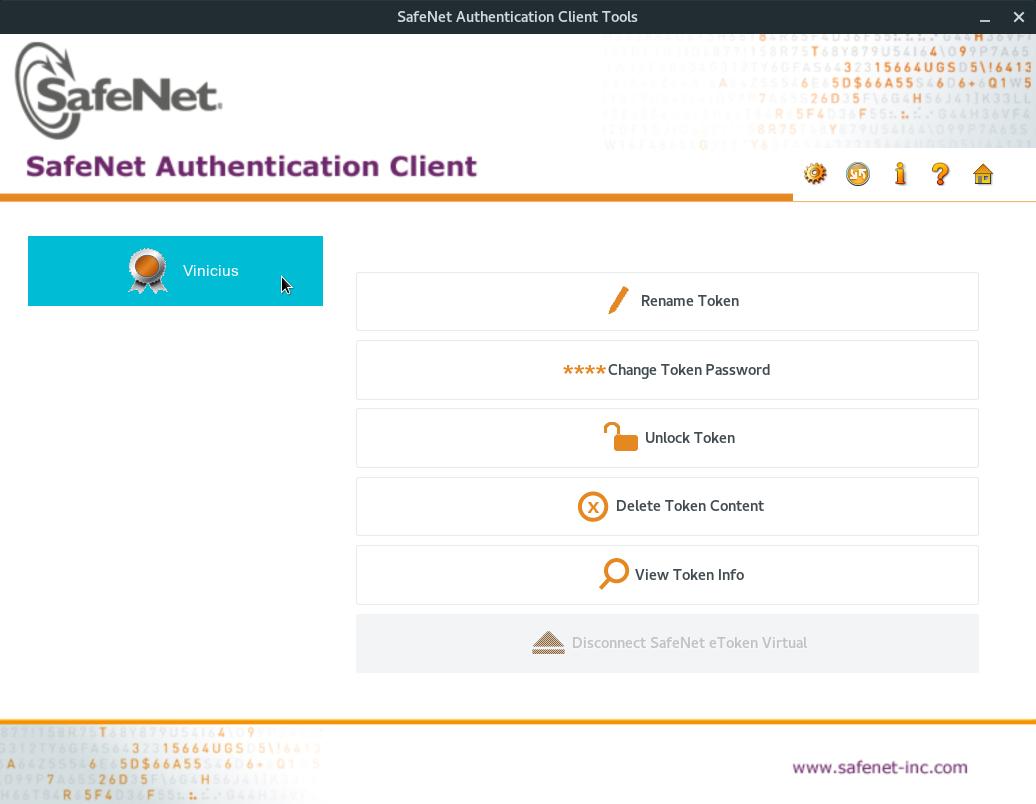
Then, to start SAC, click on Activities, on the top-left screen corner, start typing safenet and click on the SafeNet Authentication Client Tools icon:
(in doubt, try clicking both icons, it happens to me too)
Note that SAC correctly recognizes your token:
Setting up the browser to use your token
In order to log in to a website using your token, you need to set up your browser first.
Before that, make sure to add your CA certificate to your browser, otherwise it won’t be able to validate your certificate hierarchy. For more information, please read:
Let’s see how to set up the Mozilla Firefox browser to use your token.
If you are looking for instructions for either Google Chrome or Chromium browsers, click here.
Start Mozilla Firefox. Open the Firefox menu (top right corner of the window) and click Preferences.
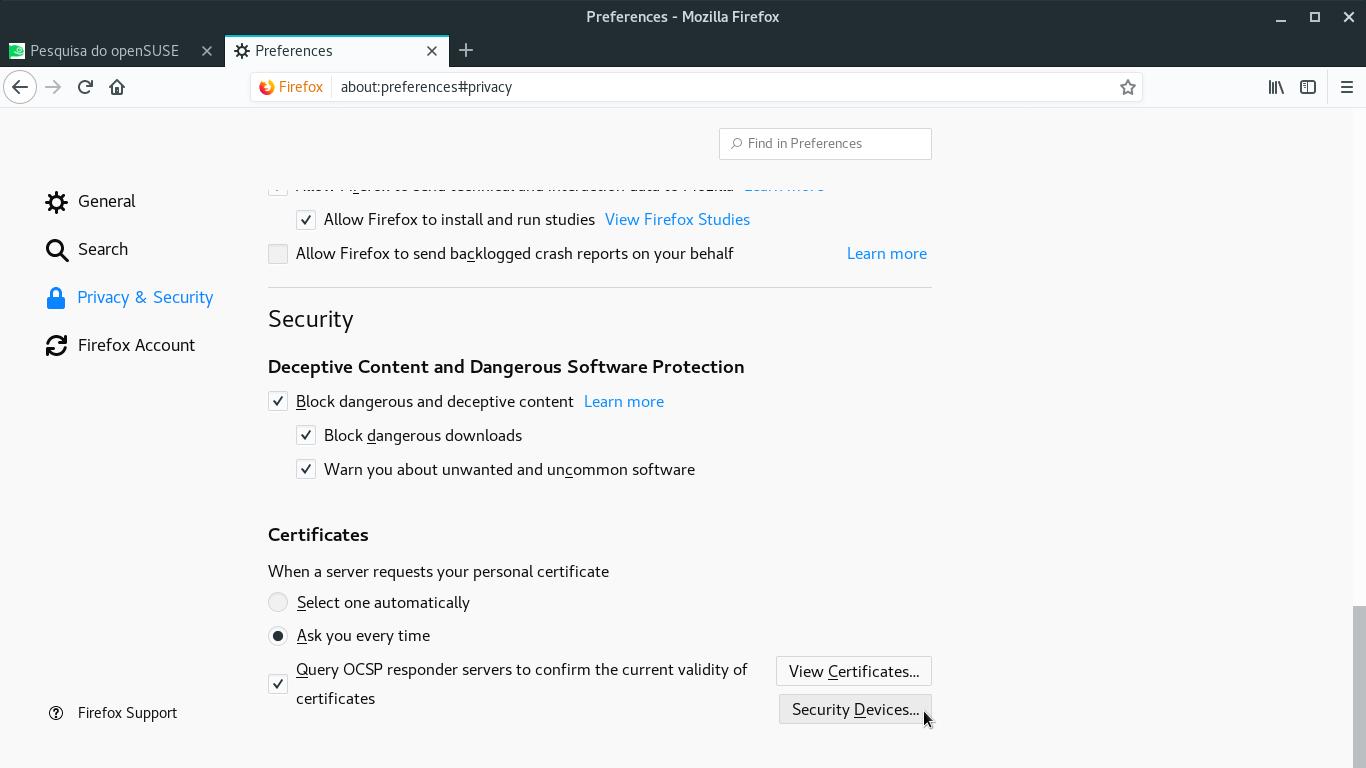
By the left, select Privacy & Security. Scroll down and click the Security Devices button:
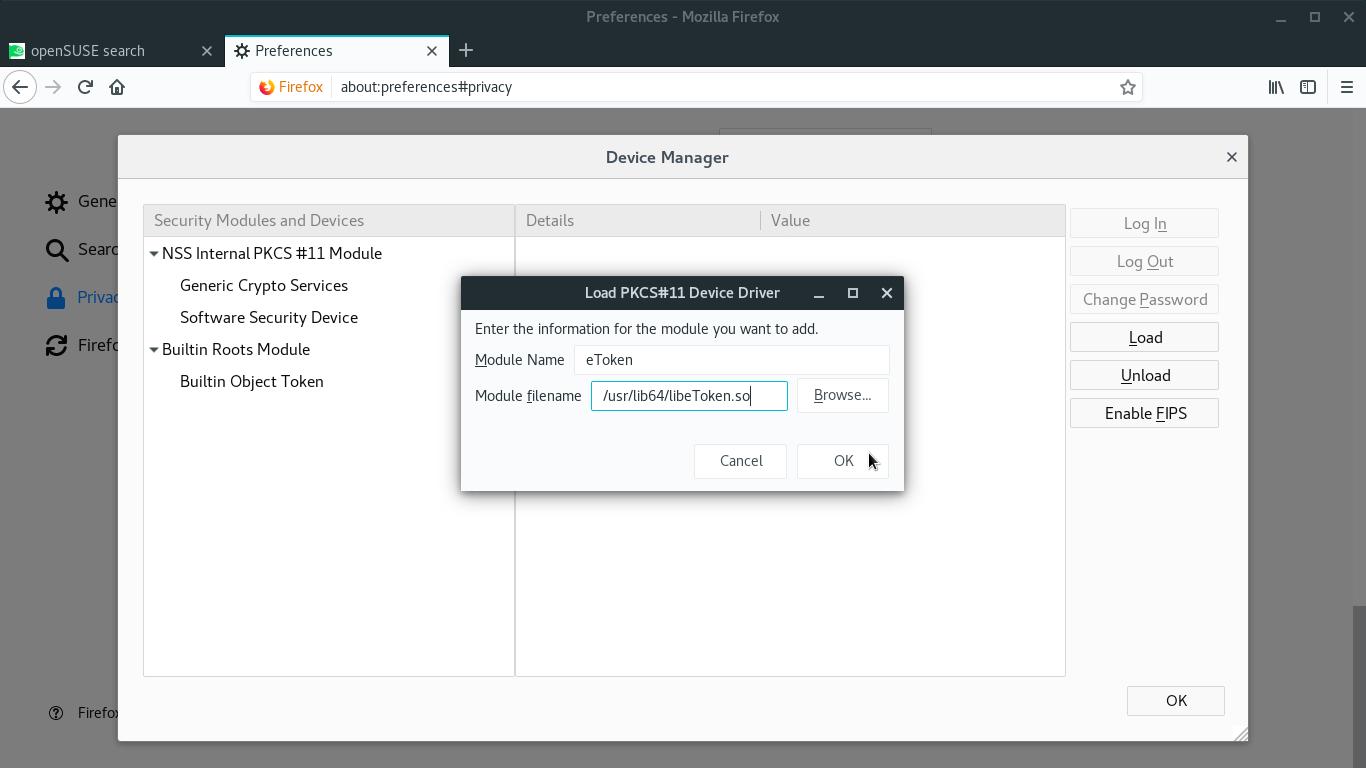
On the Device Manager dialog box, click Load.
On the next dialog box, fill in the Module Name field with a name that identifies your token (for instance, eToken).
Fill in the Module filename field with the path to your token’s library:
- if your token is supported by OpenSC, type
/usr/lib64/opensc-pkcs11.so; - if you have a SafeNet token and needed to install SAC (like me), type
/usr/lib64/libeToken.so; - for other token models, ask your token vendor or your certificate authority which path should be informed.
When you finish, click OK:
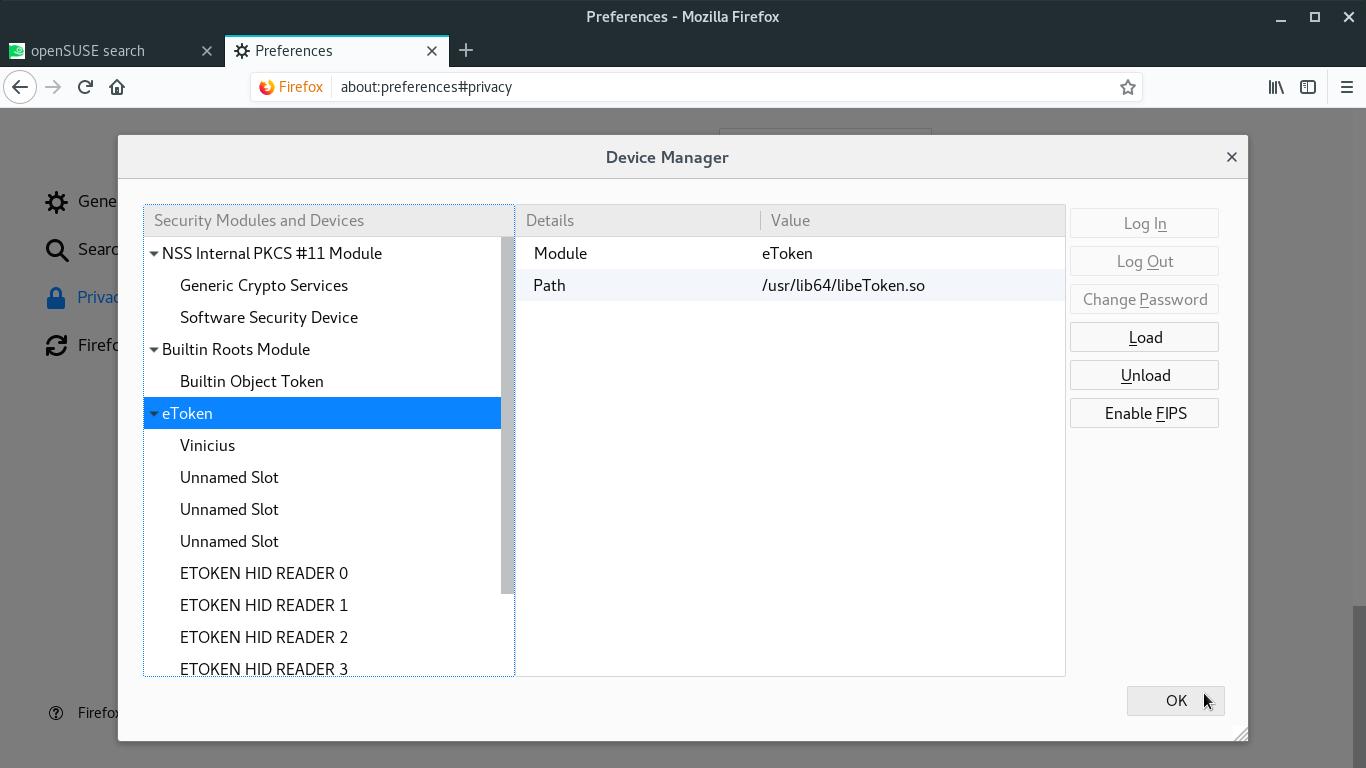
Your token is added to the list of Security Modules and Devices. Click OK:
Logging in to a website using a digital certificate
Let’s see how to access a smart card enabled website with Mozilla Firefox.
As I live in Brazil, I’m going to use Brazilian eCAC as example. Use whatever smart card enabled website you may have access.
Make sure your smart card is plugged in.
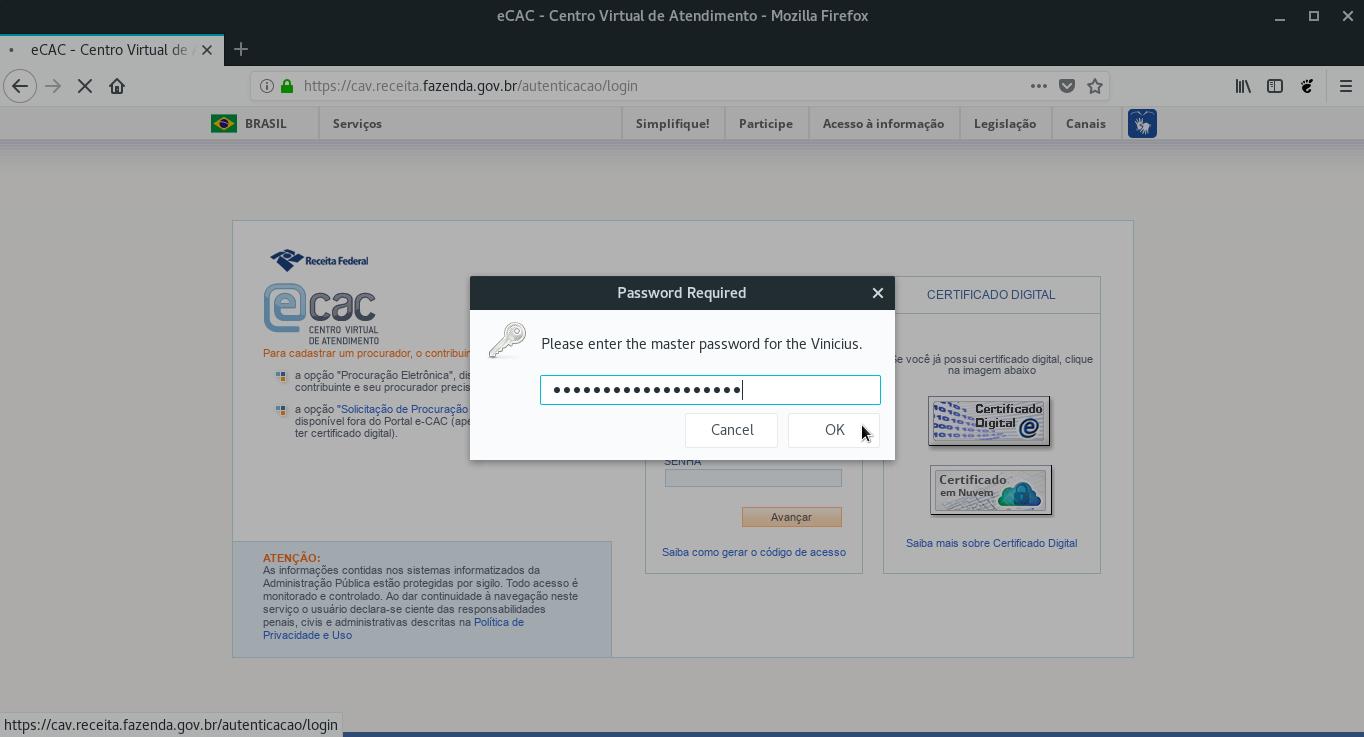
Navigate to your chosen website and choose to log in using your digital certificate.
Enter the PIN for your smart card and click OK:
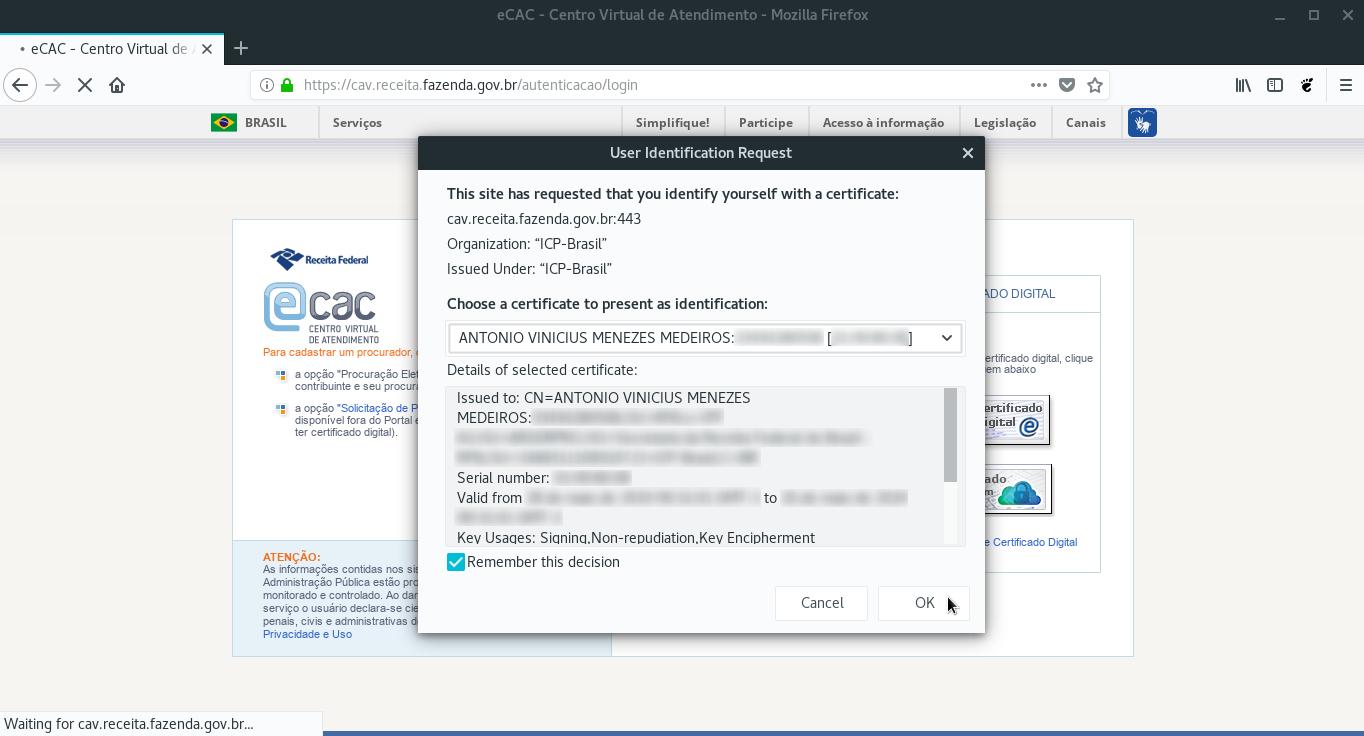
Select the certificate to use and click OK:
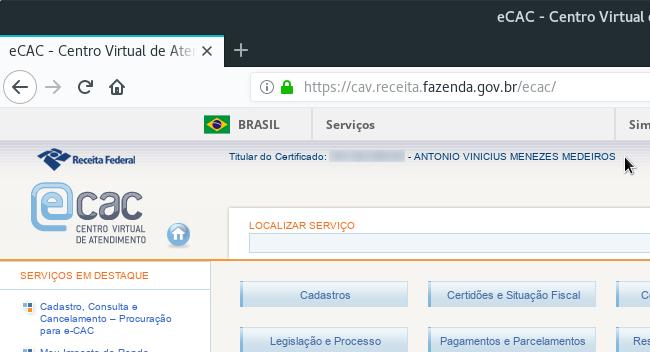
Check the website displays your information and you successfully logged in:
Now you are ready to access websites with your smart card and use it in other applications.
See how you can use your digital certificate in openSUSE:
Have a lot of fun!
References
- DoD Common Access Card (CAC) Reader - openSUSE Wiki
- Configuring Smart Card authentication on SUSE Linux Enterprise - SUSE Communities
- Use a DoD smartcard to access CAC enabled websites - Fedora Magazine
- Aladdin eToken PRO · OpenSC/OpenSC Wiki · GitHub
- Unsuported Aladdin eToken PRO USB 72k Java · Issue #461 · OpenSC/OpenSC · GitHub
- SafeNet Authentication Client Administrator’s Guide
- Installing OpenSC PKCS#11 Module in Firefox, Step by Step · OpenSC/OpenSC Wiki · GitHub
- DER vs. CRT vs. CER vs. PEM Certificates and How To Convert Them
- Howto use Aladdin eToken under Linux - René Mayrhofer