Today you are going to see how to set up the Google Chrome web browser to use digital certificates stored on criptographic media, such as smart cards or tokens. Same instructions for Chrome apply to its open source base Chromium. To test your setup, you are going to log in to a smart card enabled website using your certificate.
For future reference, here I use Linux Kamarada 15.1 Beta (based on openSUSE Leap 15.1).
Previous reading
Before starting, to get everyone on the same page, I recommend reading previous posts about digital certificates:
- How to install website certificates on Linux: here you are going to see how to install the CA certificate on Chrome
- Using smart cards on openSUSE Linux: here you are going to see how to install support for smart cards and tokens (you don’t need to read from the browser configuration part to the end, which is what we are going to do here, but using Chrome instead of Mozilla Firefox, which was the browser used in that post)
Setting up Chrome to use your token
Chrome for Linux manages digital certificates similarly to Firefox — using Mozilla NSS as backend. But, unlike Firefox, Chrome does not provide a graphical user interface to install PKCS11 modules. So, to set up Chrome you need to use the command line.
Plug in your token before proceeding.
First, start by opening the terminal and installing Mozilla NSS Tools (they may be already installed on your system):
1
# zypper in mozilla-nss-tools
Then, make sure you are on your home folder and run the following command (making the appropriate substitutions) to add your token to the list of security modules and devices:
1
2
$ cd
$ modutil -dbdir sql:.pki/nssdb/ -add "token_name" -libfile /path/to/library
Replace token_name by a name that identifies your token (for instance, eToken).
Replace /path/to/library with the path to your token’s library:
- if your token is supported by OpenSC, type
/usr/lib64/opensc-pkcs11.so; - if you have a SafeNet token and needed to install SAC (like me), type
/usr/lib64/libeToken.so; - for other token models, ask your token vendor or your certificate authority which path should be informed.
I currently use a SafeNet eToken 5110. So, for me, that command ended like this:
1
$ modutil -dbdir sql:.pki/nssdb/ -add "eToken" -libfile /usr/lib64/libeToken.so
modutil alerts you that you need to close your browser:
1
2
3
4
WARNING: Performing this operation while the browser is running could cause
corruption of your security databases. If the browser is currently running,
you should exit browser before continuing this operation. Type
'q <enter>' to abort, or <enter> to continue:
Close any running web browsers and hit Enter. When the command finishes, you can reopen them:
1
Module "eToken" added to database.
You can verify that the token has been successfully added by running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
$ modutil -dbdir sql:.pki/nssdb/ -list
Listing of PKCS #11 Modules
-----------------------------------------------------------
1. NSS Internal PKCS #11 Module
uri: pkcs11:library-manufacturer=Mozilla%20Foundation;library-description=NSS%20Internal%20Crypto%20Services;library-version=3.45
slots: 2 slots attached
status: loaded
slot: NSS Internal Cryptographic Services
token: NSS Generic Crypto Services
uri: pkcs11:token=NSS%20Generic%20Crypto%20Services;manufacturer=Mozilla%20Foundation;serial=0000000000000000;model=NSS%203
slot: NSS User Private Key and Certificate Services
token: NSS Certificate DB
uri: pkcs11:token=NSS%20Certificate%20DB;manufacturer=Mozilla%20Foundation;serial=0000000000000000;model=NSS%203
2. eToken
library name: /usr/lib64/libeToken.so
uri: pkcs11:library-manufacturer=SafeNet,%20Inc.;library-description=SafeNet%20eToken%20PKCS%2311;library-version=9.0
slots: 10 slots attached
status: loaded
slot: AKS ifdh [eToken 5110 SC] 00 00
token: Vinicius
uri: pkcs11:token=Vinicius;manufacturer=SafeNet,%20Inc.;serial=026a102c;model=eToken
slot:
token:
uri: pkcs11:
slot:
token:
uri: pkcs11:
slot:
token:
uri: pkcs11:
slot: ETOKEN HID READER 0
token:
uri: pkcs11:
slot: ETOKEN HID READER 1
token:
uri: pkcs11:
slot: ETOKEN HID READER 2
token:
uri: pkcs11:
slot: ETOKEN HID READER 3
token:
uri: pkcs11:
slot:
token:
uri: pkcs11:
slot:
token:
uri: pkcs11:
-----------------------------------------------------------
Logging in to a website using a digital certificate
Let’s see how to access a smart card enabled website with Chrome.
As I live in Brazil, I’m going to use Brazilian eCAC as example. Use whatever smart card enabled website you may have access.
Make sure your smart card is plugged in.
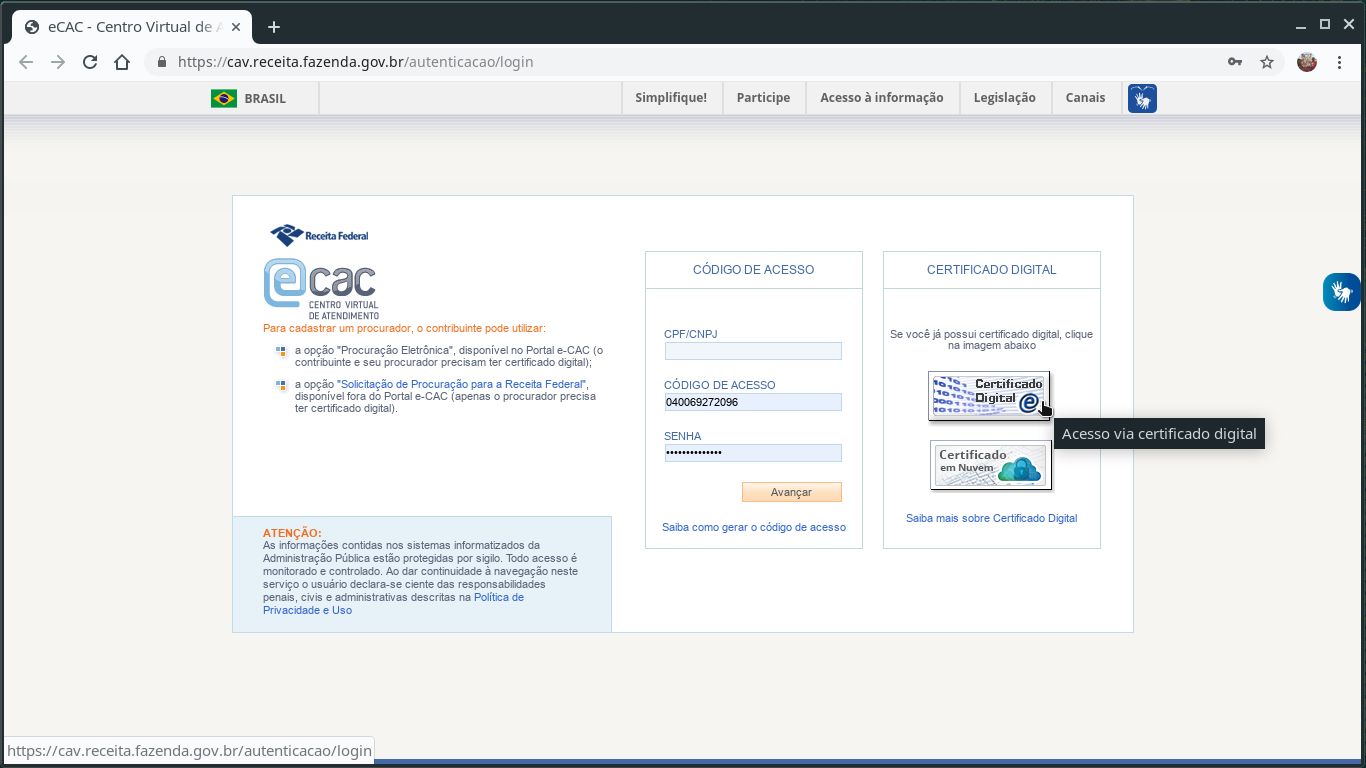
Navigate to your chosen website and choose to log in using your digital certificate:
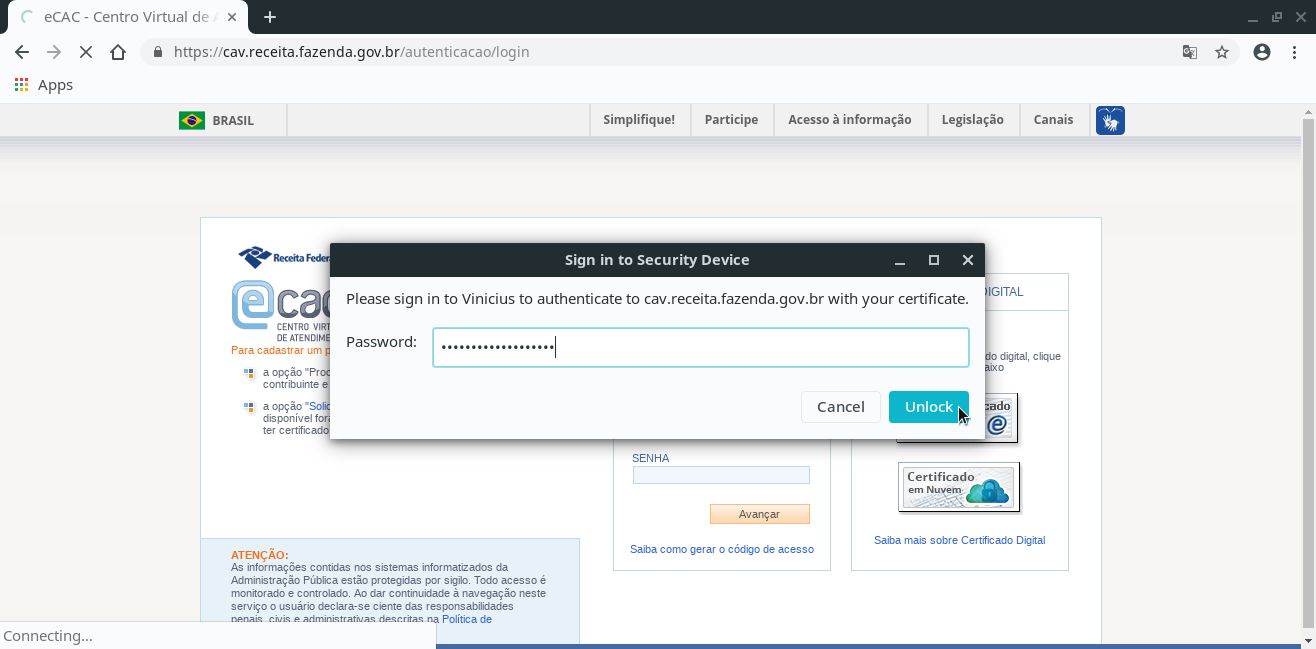
Enter the PIN for your smart card and click Unlock:
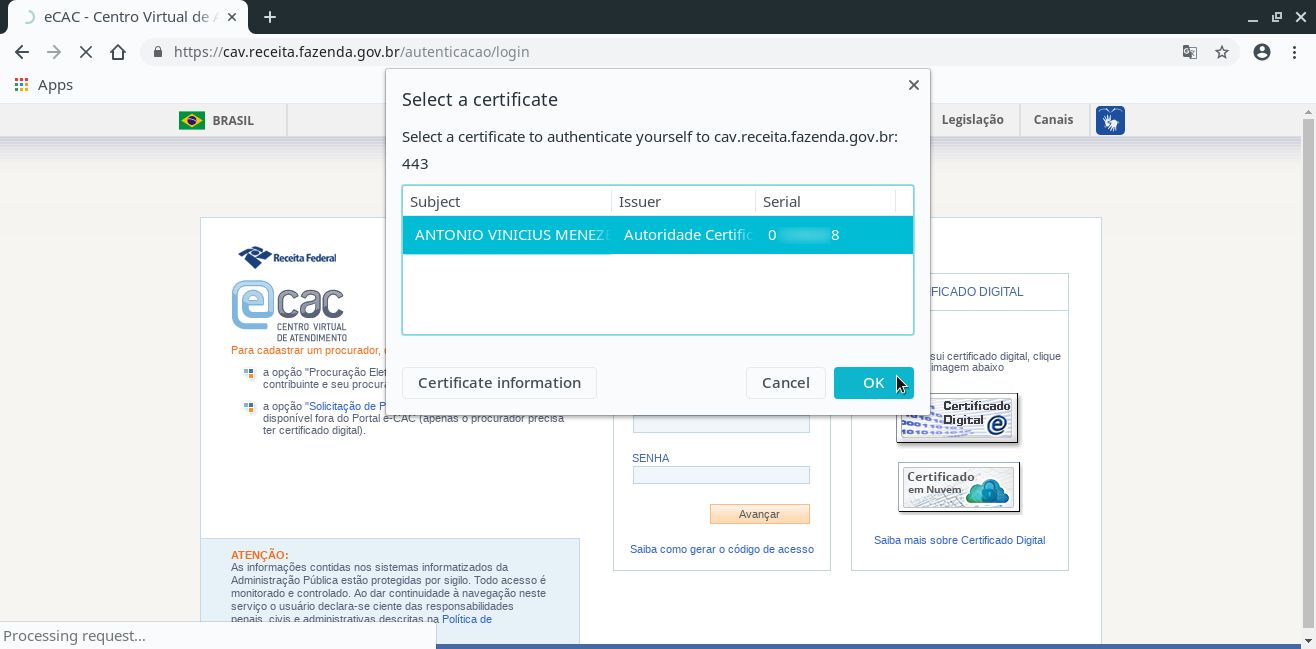
Select the certificate to use and click OK:
Check the website displays your information and you successfully logged in:
Now you are ready to access websites with your smart card and use it in other applications.
Have a lot of fun!
Further reading
See how you can use your digital certificate in openSUSE: